Moonstone Sleet Persisting Threat: The Quest to Counteract WordPress Hacks
It’s August 6, 2024 — the day when the digital media ecosystem is once again reverberating with news of a potential cybersecurity threat. This time, it’s about a suspectedNorth Korea-linked worry named ‘Moonstone Sleet propagating malicious npm packages to the JavaScript package registry. This is alarming, mainly because the mission is to infect Windows systems, highlighting the unrelenting nature of the menace.
Clean WordPress hack and repair the hacked WordPress site—that’s the need of the hour. WordPress protection has never been this critical!
The malicious npm packages in question—harthat-api and harthat-hash—were released on July 7, 2024, tracked by the ever-vigilant Datadog Security Labs. They emitted a degree of concern because, although the libraries failed to draw any downloads and were removed shortly thereafter, the presence of such packages in the wild remains a significant risk.
Clustered together as a differentiated North Korean malevolent activity group known as “Moonstone Sleet,” Datadog is closely monitoring the activities of this threat actor under the tag ‘Stressed Pungsan’.
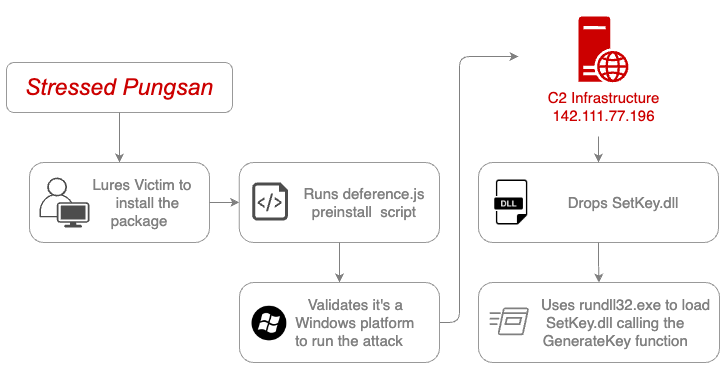
It has come to light that the adverse collective, known for circulating counterfeit ZIP archive files through platforms like LinkedIn, uses forged company names or freelancing websites to trick potential victims. The unsuspecting users, lured by an alleged technical skills evaluation, end up executing payloads that invoke an npm package.
One primary strategy appeared to be the use of the malicious package ‘curl’ that connects to an IP controlled by the actor and subsequently downloads additional injurious payloads like SplitLoader. In another instance, Moonstone Sleet was noted to be delivering an npm loader embedded with malicious intent leading to credential theft from LSASS.
Subsequent revelations confirmed that Moonstone Sleet was also attempting to infect the npm registry by spreading their packages. The newly discovered packages are designed specifically to run a pre-installation script dictated by the package.json file. Post-checking its operation on a Windows system (“Windows_NT”), it would establish contact with an external server (“142.111.77[.]196”), resulting in the download of a DLL file that’s sideloading using the rundll32.exe binary.
A point of intrigue remains the rogue DLL. It doesn’t implement active malice, sparking speculation about a trial run of its payload delivery infrastructure or if it was an inadvertent push to the registry before the insertion of malicious code.
The news comes in quick succession to reports of cyberattacks by North Korean threat groups identified as Andariel and Kimsuky by South Korea’s National Cyber Security Center (NCSC). Andariel and Kimsuky are notorious for delivering malware families such as Dora RAT and TrollAgent (aka Troll Stealer) in their intrusion campaigns targeting construction and machinery sectors in the country. Ostensibly, the Andariel hackers have adopted the tactic of exploiting vulnerabilities in a domestic VPN software’s software update mechanism to disseminate Dora RAT, a malware.
In today’s world, it’s more important than ever to emphasize the importance of clean WordPress hack strategies, repair hacked WordPress sites, and overall WordPress protection. It’s a veritable tug of war between threat actors and security professionals, but with vigilance and robust security measures, a clean and secure digital future is attainable.
Need security services for your WordPress site? Contact DrGlenn for protection and recovery. Order Services Today!.